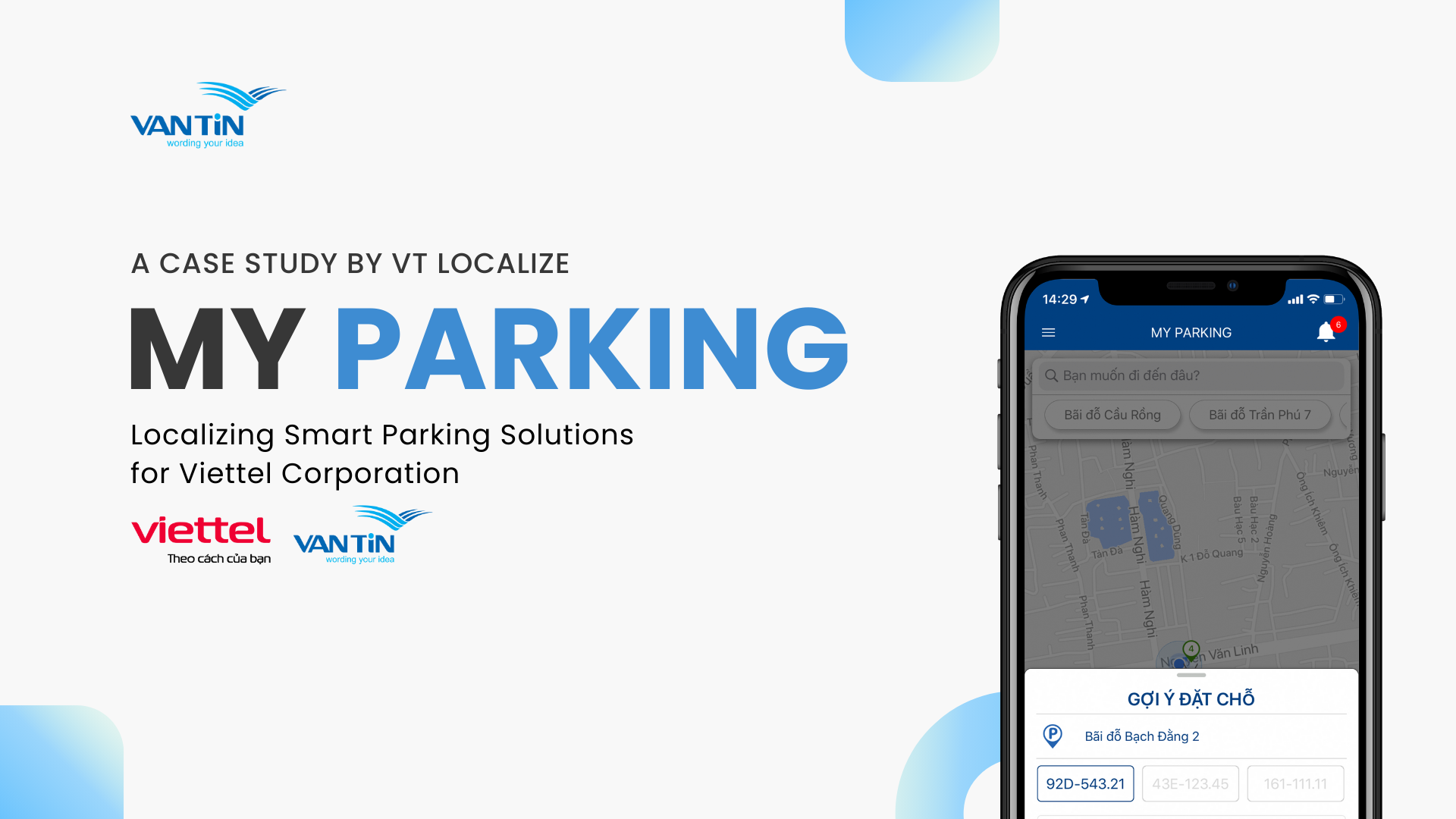
As a end result, an automated SMS textual content message might be sent to the infrastructure group, prompting them to increase the server’s capacity or add additional area to the disk quantity. Similarly, a “multiple failed login attempts” event can trigger a network configuration change blocking the offending IP handle and alerting the SecOps team. Continuous monitoring can be traced again to its roots in traditional auditing processes. While all of those strategies may be effective for monitoring and evaluating financial plans, the best suited choice will depend on the corporate’s specific needs and aims.

overseas body reaction in an effort to improve the tolerability of completely implantable devices. Previous efforts have focused on implanted artificial continuous monitoring cloud polymer coatings with or without concomitant use of anti-inflammatory brokers to combat the host tissue response to the implanted sensor device.
Importance Of Continuous Monitoring
Continuous monitoring can even assist businesses improve their operational effectivity by figuring out areas the place they will optimize their processes. For example, companies can monitor their stock ranges to determine potential stock-outs or overstocking. They also can monitor their production processes to identify bottlenecks or alternatives to streamline their operations.
- If you switch, store, or process information exterior the EU or UK, identify your authorized basis for the info transfer.
- Continuous monitoring may help companies meet compliance necessities by offering real-time visibility into their safety posture.
- Stop loss orders are significantly useful in risky markets, as they defend your capital from important fluctuations.
- Continuous high quality monitoring in DevOps is the process of figuring out threats to the security and compliance rules of a software program growth cycle and architecture.
- In addition to the security benefits, steady monitoring also can help businesses to improve their operational efficiency.
The key parts of continuous monitoring embrace automated data collection, analysis, reporting, and response. Automated data collection entails gathering data from varied sources, such as system logs, community traffic, and utility activity. Automated evaluation involves using instruments and technologies to investigate and interpret the data to identify points, dangers, and potential threats. Automated reporting entails producing reviews that present insights into system performance, vulnerabilities, and compliance.
Continuous monitoring and adjustments allow yield managers to be flexible in pricing. By doing so, yield managers can optimize income and keep away from overpricing or underpricing. For instance, if demand is excessive, yield managers can improve prices to maximize revenue.
Advanced threat protection is a sort of cybersecurity devoted to stopping pre-planned cyberattacks, such as malware or phishing. Active Directory Bridging is a expertise in the subject of networking that aims to enhance the communication… Access control lists (ACL) control or restrict the flow of site visitors by way of a digital environment. StrongDM Team, Dynamic Access Management platform, StrongDM puts individuals first by giving technical workers a direct route to the critical infrastructure they have to be their most productive.
The Ability Of Continuous Monitoring And Feedback In Devops: Unlocking Success In A Dynamic Panorama
There are several choices for implementing steady monitoring and analysis, including guide processes, spreadsheets, and specialized software. When selecting the greatest choice, organizations ought to consider their specific needs and price range constraints. One such instance is Toyota, which had implemented a complete risk management system that included steady monitoring of its provide chain. Through this system, Toyota was in a position to establish potential risks early on and proactively develop contingency plans. When the disaster struck, the company shortly activated its response plan, redirecting supplies and assets to minimize disruptions.
For instance, if access administration is a important management for your organization, you should listing the key methods and arrange regular reviews of consumer entry rights as part of your small business processes. Monitoring and analysis can improve accountability by offering organizations with information and proof to support their decision-making. By monitoring progress towards objectives and goals and reporting on efficiency, organizations can reveal their commitment to accountable and efficient risk management.
Chaos Engineering In Devops: Embracing Failure To Enhance Resilience
However, if demand abruptly drops, yield managers can quickly modify costs to keep away from shedding gross sales. Utilize technology and automation instruments to streamline knowledge collection and analysis processes. Diversifying your buying and selling portfolio entails spreading your risk throughout completely different forex pairs, asset lessons, and geographical regions. By diversifying, you’ll have the ability to reduce the influence of base foreign money volatility in your overall portfolio. For instance, when you have a major exposure to a particular forex and its value plummets unexpectedly, having other currency pairs in your portfolio might help offset potential losses. The integrations are the most effective method for acquiring most output from CM instruments and methods.
By setting a cease loss order, you determine a predetermined exit level for a commerce, routinely closing it if the market strikes in opposition to your place. Stop loss orders are particularly useful in volatile markets, as they protect your capital from significant fluctuations. It is essential to set stop loss ranges based mostly on careful analysis, considering factors such as support and resistance levels, latest market trends, and overall market sentiment. When it comes to adjusting threat management methods, it is essential to suppose about numerous perspectives. Traders usually fall into the entice of relying solely on historical information or technical indicators, neglecting the significance of basic analysis. While historic data can provide insights into past market conduct, it could not accurately reflect the current market circumstances.
CM is the process that entails faster identification of safety dangers and compliance points in the IT infrastructure. It is probably one of the vital tools that support the SecOps (Security and Operations) teams by providing data from numerous public and hybrid cloud environments. In addition, steady monitoring additionally supplies assist for critical safety processes such as root cause evaluation, incident response, and menace intelligence. In at present’s rapidly evolving technological panorama, organizations face a continuing barrage of cyber threats. Implementing continuous monitoring may help organizations detect and reply to these threats rapidly, minimizing potential harm and decreasing the risk of information breaches.

The steady audit is among the supporting steady monitoring of finest practices that enhance the general course of. Obtaining information from all features of the IT infrastructure of a company just isn’t the solely real purpose of CM. Users ought to consider the continuously rising and centralized data daily on a consistent basis. As organizations have set about to institute compliance packages, they have learned they have to give you new methods for maintaining that compliance. It could be a key component of finishing up the quantitative judgement part of an organization’s overall enterprise threat administration.
The final step in implementing steady monitoring is to combine it with current systems and processes. This includes ensuring that the tools and technologies are compatible with the present systems, such because the IT infrastructure, software program applications, and security protocols. It’s additionally essential to guarantee that the monitoring program doesn’t disrupt or impact the normal operations of the organization. Continuous monitoring is an essential software for companies that need to stay forward of potential threats and vulnerabilities. This, in flip, helps companies to enhance their overall resilience and scale back the chance of costly security breaches. Continuous monitoring and analysis may help organizations improve their performance by identifying areas for improvement and implementing adjustments to address them.
DevOps, a fusion of improvement and operations, goals to break down silos, improve collaboration, and accelerate software delivery. While the adoption of DevOps ideas has proven beneficial for lots of organizations, it’s important to recognize that it’s not a one-time implementation; rather, it’s a continuous journey of enchancment. Among the critical components that drive success in DevOps, steady monitoring and feedback play a pivotal role.
By figuring out underperforming investments, evaluating strategies, and capitalizing on market trends, companies can optimize their ROI. By following the tips and studying from case studies, firms can effectively implement steady monitoring and evaluation to drive higher returns on their investments. One of the necessary thing benefits of steady monitoring is the ability to establish and handle issues early on. By often tracking and analyzing knowledge, we can establish any deviations from our expected outcomes and take quick action to rectify them. Through continuous monitoring, you discover that the team is falling not on time. By shortly identifying this deviation, you’ll find a way to allocate extra resources or regulate the project timeline to make sure that the project stays on track.
Continuous monitoring can use logs, metrics, traces, and events as its information sources for each area. In this article, we’ll specifically focus on steady monitoring via logs. In this text, we will cowl the assorted types https://www.globalcloudteam.com/ of steady monitoring, the advantages it delivers, and a few best practices for efficiently constructing a steady monitoring regimen. For example, suppose you’re operating a multi-tier net and mobile utility with many moving elements.